Mirror real-world attack behavior and gain actionable insights into exploitable weaknesses of your Web Applications and APIs.

Find vulnerabilities before attackers do with comprehensive security testing engine.
Improve your security posture with actionable findings and clear remediation guidance.
Meet compliance requirements with evidence-based reporting and detailed documentation.
Experience full-spectrum security analysis without the complexity.
Our proprietary scanning engine, built by security researchers and penetration testers, powers the platform that delivers fast, accurate and actionable security insights.
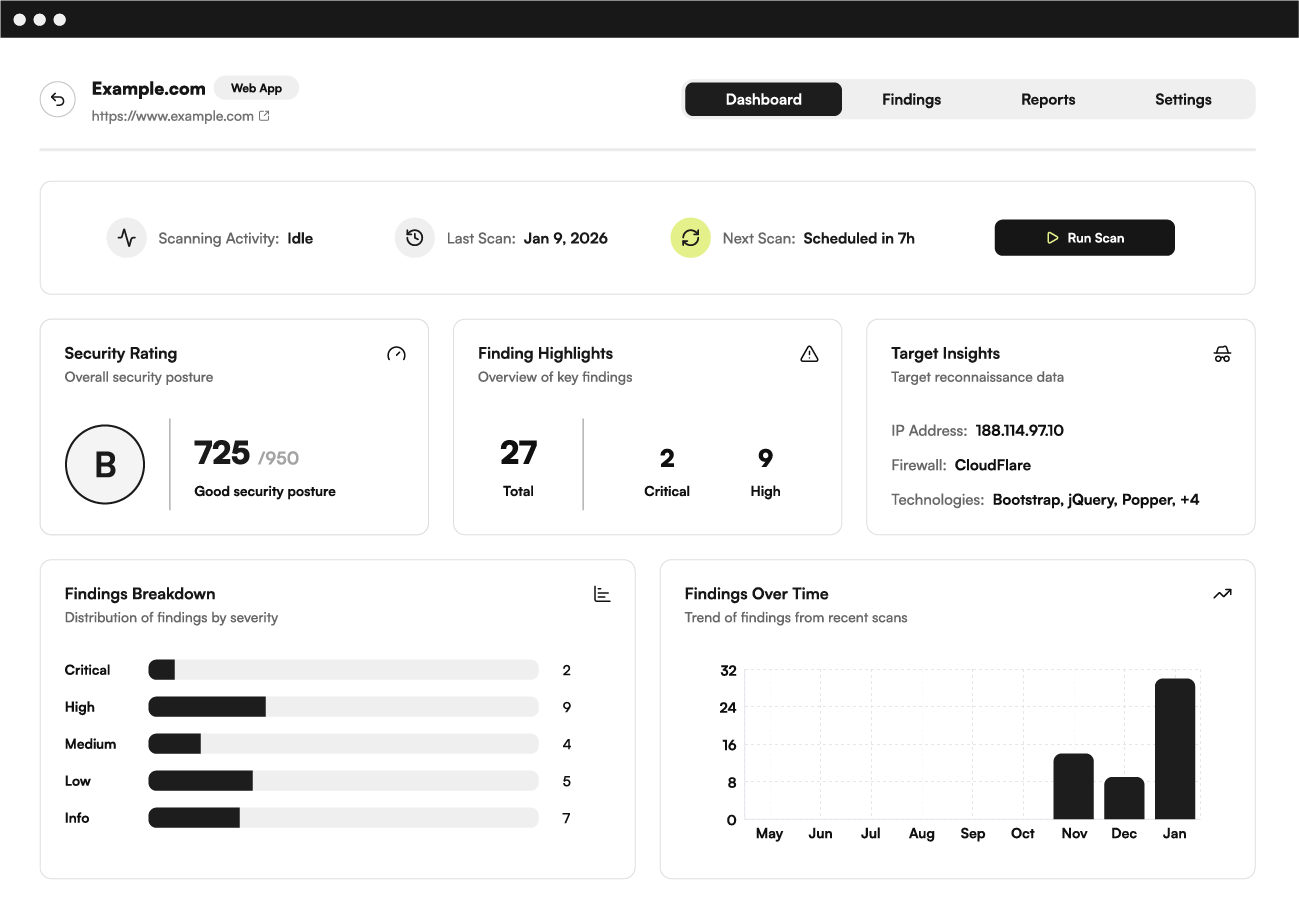
Get started in minutes with our streamlined security testing workflow.
Simply specify the assets you want to test, and you’ll be ready to start in minutes.
Our advanced platform identifies vulnerabilities, misconfigurations, and security gaps.
Receive prioritized findings with clear remediation guidance to strengthen your security.
Designed for continuous discovery, detailed remediation and clear reporting.

Every vulnerability comes with context. Clear, step-by-step guidance including recommended fixes and practical examples. No security degree required.

Scan your application from the inside out. Authenticated scanning uses valid credentials to access protected areas, enabling deeper coverage across user-only functionality, business logic, and role-based access paths for more accurate and actionable findings.

Stay ahead of new vulnerabilities with automated daily scans. Continuous scanning monitors your application for changes and emerging risks, ensuring new issues are detected as soon as they appear.
Turn complex security data into easy-to-understand reports for teams, managers and auditors.


Examples of real-world scenarios where our platform makes an impact.

Establish ongoing monitoring of application exposure alongside compliance-ready evidence that support risk oversight and security posture assurance.

Test running applications from an attacker’s perspective and validate changes to understand how code and configuration updates impact application exposure before release.
Choose the plan that fits your security needs. No hidden fees, no surprises.
Best for essential protection and early-stage teams.
Best for continuous protection and growing teams.
Don't hesitate to contact us for custom needs.
Got questions? We've got answers. Here's what people ask us most before getting started.
Launch a security assessment and protect your application against real threats.
Get Started